Tag VLAN
スイッチ同士をTag接続して、Tagリンクを複数のVLANに所属させる
複数のスイッチを介してVLANが構築できることを確認する
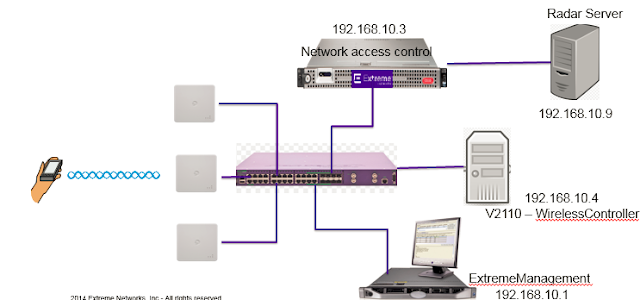
ネットワーク構成
複数のVLANが所属するポートのことをTag ポートと呼びます。
複数のスイッチを介してVLANを構成する場合は、スイッチ同士がつながるポートをTagポートにします。
Untag ポートでは、一つのVLANにしか所属できません。
しかし、1個のポートに複数のVLANのデータが行う場合もあります。
その場合、そのポートをTagポートに設定します。
ポートをTagポートに設定すると、そのポートでMACフレームにVLAN情報を加えて送り出すようになります。
show commands で確認する
##### Switch-1 のコンフィグ #####
* X480-24x.14 # show vlan "Sale"
VLAN Interface with name Sale created by user
Admin State: Enabled Tagging: 802.1Q Tag 100
Description: For Sale team PC
Virtual router: VR-Default
IPv4 Forwarding: Disabled
IPv4 MC Forwarding: Disabled
IPv6 Forwarding: Disabled
IPv6 MC Forwarding: Disabled
IPv6: None
STPD: None
Protocol: Match all unfiltered protocols
Loopback: Disabled
NetLogin: Disabled
OpenFlow: Disabled
TRILL: Disabled
QosProfile: None configured
Egress Rate Limit Designated Port: None configured
Flood Rate Limit QosProfile: None configured
Ports: 2. (Number of active ports=0)
Untag: 25
Tag: 24
* X480-24x.15 # show vlan "Engineer"
VLAN Interface with name Engineer created by user
Admin State: Enabled Tagging: 802.1Q Tag 200
Description: For Engineer team PC
Virtual router: VR-Default
IPv4 Forwarding: Disabled
IPv4 MC Forwarding: Disabled
IPv6 Forwarding: Disabled
IPv6 MC Forwarding: Disabled
IPv6: None
STPD: None
Protocol: Match all unfiltered protocols
Loopback: Disabled
NetLogin: Disabled
OpenFlow: Disabled
TRILL: Disabled
QosProfile: None configured
Egress Rate Limit Designated Port: None configured
Flood Rate Limit QosProfile: None configured
Ports: 2. (Number of active ports=0)
Untag: 26
Tag: 24
* X480-24x.17 # show vlan description
-------------------------------------------------------------------------------
Name VID Description
-------------------------------------------------------------------------------
Default 1
Engineer 200 For Engineer team PC
Mgmt 4095 Management VLAN
Sale 100 For Sale team PC
-------------------------------------------------------------------------------
* X480-24x.20 # show config vlan
#
# Module vlan configuration.
#
configure vlan default delete ports all
configure vr VR-Default delete ports 1-26
configure vr VR-Default add ports 1-26
configure vlan default delete ports 24-26
create vlan "Engineer"
configure vlan Engineer description "For Engineer team PC"
configure vlan Engineer tag 200
create vlan "Sale"
configure vlan Sale description "For Sale team PC"
configure vlan Sale tag 100
configure ports 25 description-string "Connect to PC1"
configure ports 26 description-string "Connect to PC2"
configure vlan Default add ports 1-23 untagged
configure vlan Engineer add ports 24 tagged
configure vlan Engineer add ports 26 untagged
configure vlan Sale add ports 24 tagged
configure vlan Sale add ports 25 untagged
enable ports 24-26
Switch -2 の設定は Switch -1 と同じでございます。