Since 802.11 stations are not able to transmit and receive at the same time, when a station is transmitting a frame, it is not able to determine whether the frame was received or whether there was a collision. Therefore, every time an 802.11 radio transmits a unicast frame, the 802.11 radio that received the frame will reply with a ACK frame. 802.11 is also capable of sending a single acknowledgement for multiple unicast frames.
IF the ACK is received , the original station knows that the frame transfer was successful. All unicast 802.11 frames must be acknowledge. Broadcast and multicast frames do not require an acknowledgement.
IF any portion of a unicast frame is corrupted, the CRC will fail and the receiving 802.11 radio will not send an ACK from to the transmitting 802.11 radio. If an ACK frame is not received by the original transmitting radio, the unicast frame is not acknowledged and will have to be retransmitted.
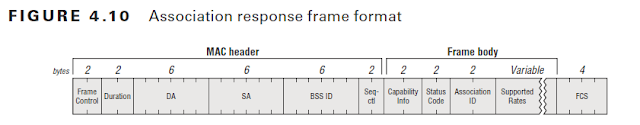
The following picture display the frame format for the ACK frame.
above the picture from CWAP
Again if an ACK frame is not received by the original transmitting radio, the unicast frame is not acknowledge and will have to be retransmitted.
Excessive layer 2 retransmissions adversely affect the WLAN in two ways:
- Layer 2 retransmissions increase overhead and therefore decrease throughput.
- If application data has to be retransmitted at layer 2, the timely delivery of application traffic becomes delay or inconsistent.